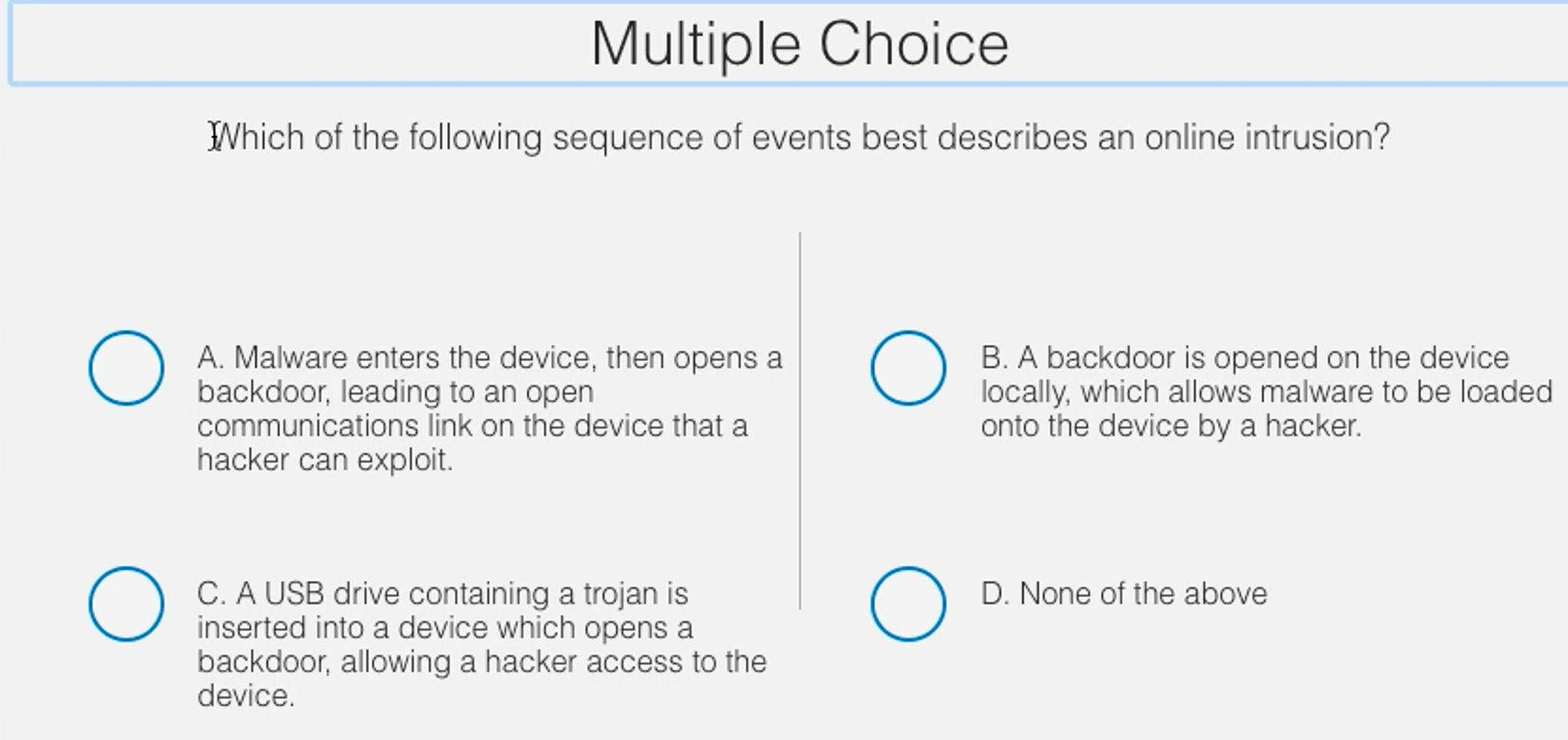
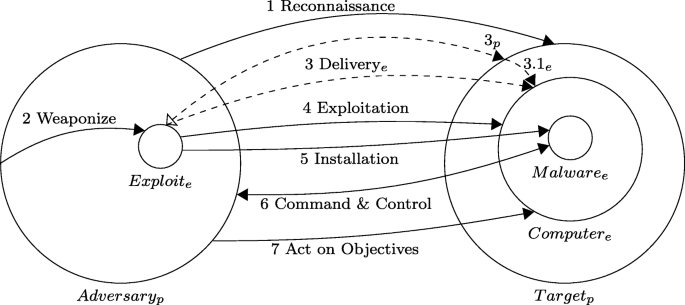
Which Of The Following Sequence Of Events Best Describes An Online Intrusion?
Which of the following sequence of events best describes an online intrusion?. Letters A B and C represent certain rocks. Which of the following BEST describes an intrusion prevention system. AA backdoor is opened on the device locally which allows malware to be loaded onto the device by a hacker.
Only the gateway shows branching of the sequence flow. An organization receives an email that provides instruction on how to protect a system from being a target of new malware that is rapidly infecting systems. She went for a walk in the forest.
The incident response team investigates the notification and determines it to invalid and notifies users to disregard the email. Pretty soon she came upon a house Then we follow her through the sequence of events upon entering the house. A backdoor is opened on the device locally which allows malware to be loaded onto the device by a hacker.
The decision diamond can depict more branching options. Which of the following Best describes this occurrenceA. B A USB drive containing a trojan is inserted into a device which opens a backdoor allowing a hacker access to the device.
Select all correct answers. Malware enters the device then opens a backdoor leading to an open communications link on the device that a hacker can exploit. An Intrusion Detection System IDS is a system that monitors network traffic for suspicious activity and issues alerts when such activity is discovered.
In this sequence of events which of the following isare true. Which of the following types of logging events are most commonly found in antivirus software. A backdoor is opened on the device locally which allows malware to.
The large cone-shaped mountain on Earths surface is a volcano. Sterling has violated Standard IV B3 Fair Dealing by not treating all his accounts equally.
Which of the following sequence of events best describes an online intrusion.
Pretty soon she came upon a house Then we follow her through the sequence of events upon entering the house. It is a software application that scans a network or a system for harmful activity or policy breaching. Only the decision diamond shows branching of the sequence flow. A system that serves as a honeypot. Franc has violated Standard IV B1 Fiduciary Duties by investing retirement account funds in the high- risk stocks. A system that stops an attack in progress. In this sequence of events which of the following isare true. AA backdoor is opened on the device locally which allows malware to be loaded onto the device by a hacker. For orders and purchases placed through our online store on this site we collect order details name institution name and address if applicable email address.
An organization receives an email that provides instruction on how to protect a system from being a target of new malware that is rapidly infecting systems. Following the sequence of events were first met with a girl named Goldilocks. Letters A B and C represent certain rocks. In this sequence of events which of the following isare true. Malware enters the device then opens a backdoor leading to an open communications link on. A backdoor is opened on the device locally which allows malware to. A system that serves as a honeypot.







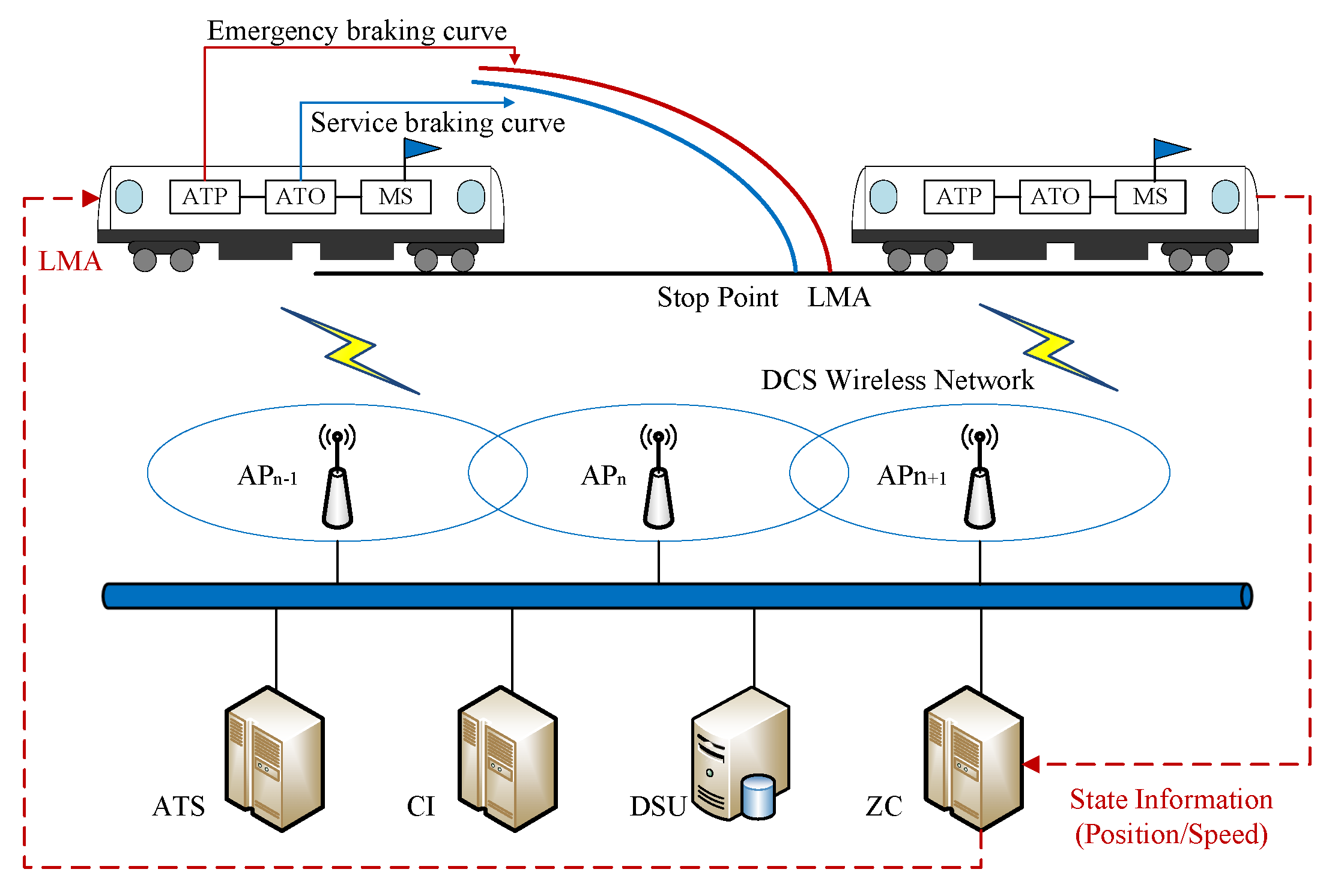

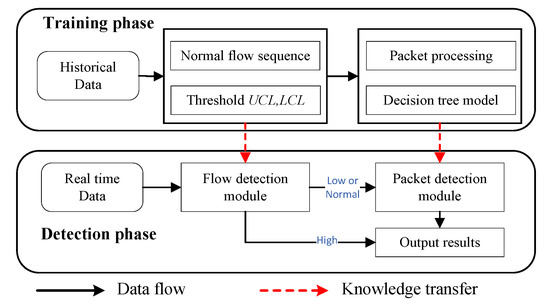
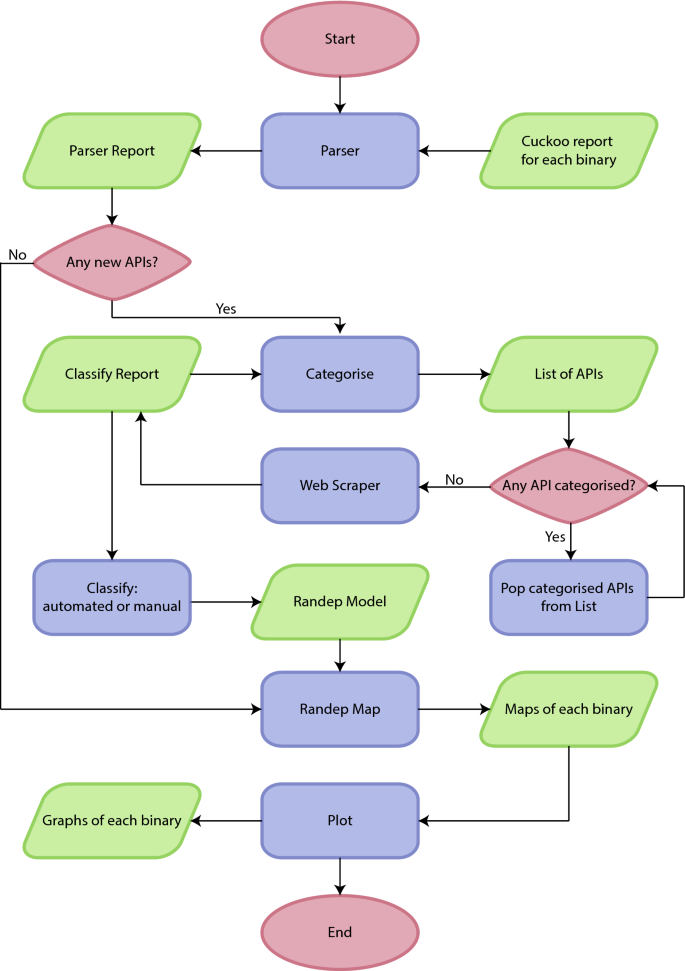
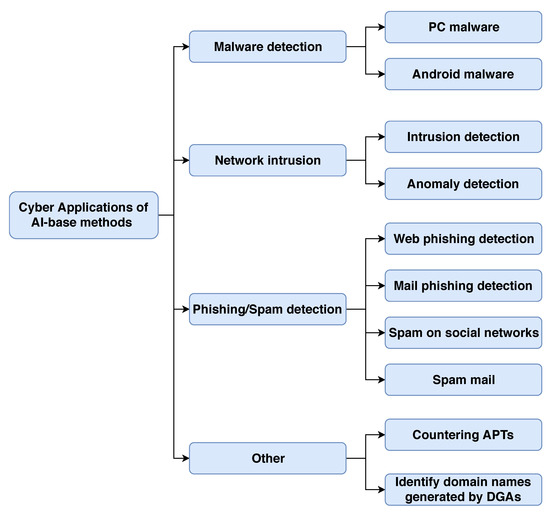










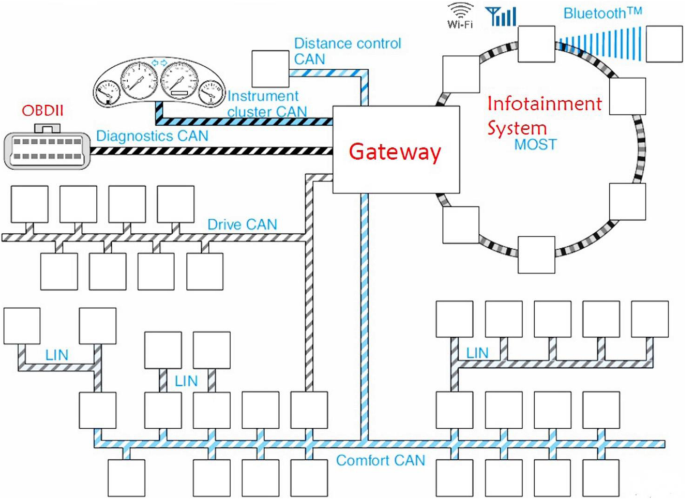
Post a Comment for "Which Of The Following Sequence Of Events Best Describes An Online Intrusion?"